What Is Network Services Virtualization?
Network services virtualization is a critical building block in network virtualization. Although all the building blocks can be deployed in isolation, network services virtualization is an excellent strategy for consolidating multiple appliances into one, simplifying network operations and reducing overall acquisition cost. Network services virtualization virtualizes a network service node such as a firewall module, for example, by partitioning the available hardware resources among different virtual firewalls. The service virtualization provides independent instances of name space, configuration, inspection engines, and other resources within each instance. Network services virtualization negates the need to acquire separate devices every time the network service is required by using the software instance on the same physical hardware. Some implementations such as the Cisco Catalyst ® 6500 Series Firewall Services Module (FWSM) can support nearly 250 separate virtual firewall instances.
Service Insertion in Physical Networks
Service insertion is a concept in virtualized networking where services can be inserted and removed at will. It is targeted toward Layer 4 through Layer 7 devices, such as firewalls and load balancers. The advantage of this approach is that it allows complex configurations to be defined quickly and from a central location.
virtualized networks including software-defined networking and network functions virtualization, one of the selling points is the flexibility of having network devices defined in software instead of hardware. With service insertion, Layer 4 through 7 devices can be mixed, matched, added and removed quickly. As enterprise networks can be very complex, spanning multiple buildings and often multiple countries, they can take a long time to configure. Software-based solutions can be managed from a central dashboard and reconfigured at will.
Some of the services targeted for service insertion include:
- Firewalls
- Load balancers
- Traffic inspection
- SSL offloading
- Application acceleration
Virtual Service Data Path
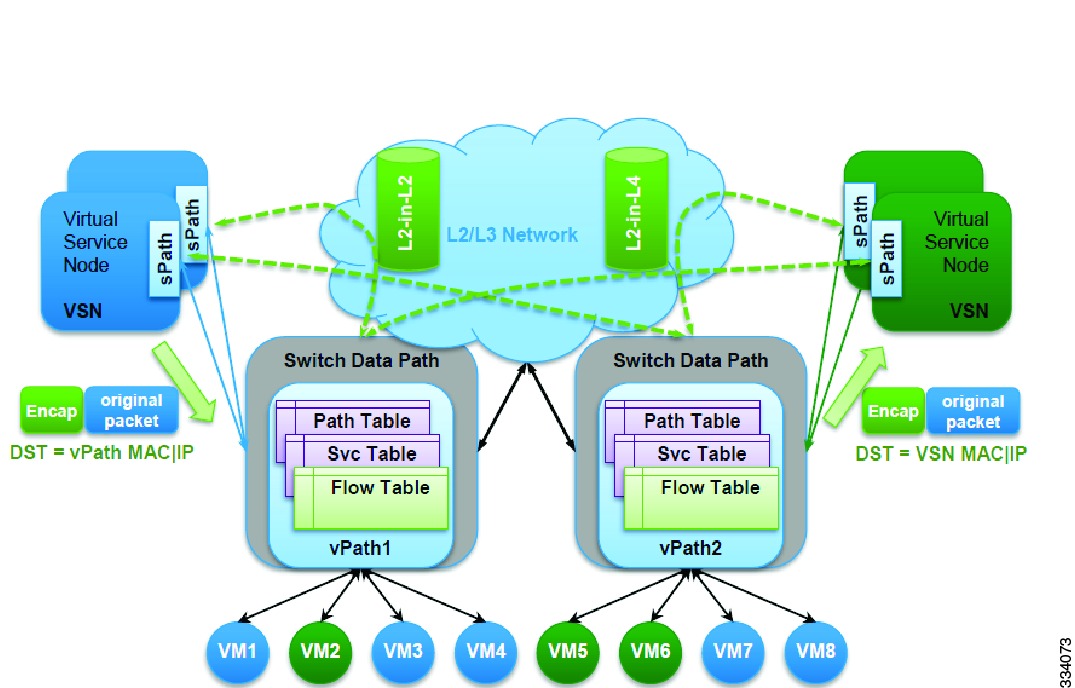
Cisco Virtual Service Data Path (vPath) is the service intelligence embedded in the Cisco Nexus 1000V Series switch.
vPath provides the forwarding plane abstraction and programmability required to implement the Layer 2 to Layer 7 network services such as segmentation firewalls, edge firewalls, load balancers, WAN optimization, and others. It is embedded in the Cisco Nexus 1000V Series switch Virtual Ethernet Module (VEM). It intercepts the traffic whether external to the virtual machine or traffic from virtual machine to virtual machine and then redirects the traffic to the appropriate virtual service node (VSN) such as Cisco Virtual Security Gateway (VSG), Cisco ASA 1000V, Cisco Virtual Wide Area Application Services (vWAAS) for processing. vPath uses overlay tunnels to steer the traffic to the virtual service node and the virtual service node can be either Layer 2 or Layer 3 adjacent.
The Cisco network virtual service (vService) is supported by the Cisco Nexus 1000V using the vPath. It provides trusted multitenant access and supports the VM mobility across physical servers for workload balancing, availability, or scale.
The basic functions of vPath includes traffic redirection to a virtual service node (VSN) and service chaining. Apart from the basic functions, vPath also includes advanced functions such as traffic off load, accleration and others.
vPath steers traffic, whether external to the virtual machine or from a virtual machine to a virtual machine, to the virtual service node. Initial packet processing occurs in the VSN for policy evaluation and enforcement. Once the policy decision is made, the virtual service node may off-load the policy enforcement of remaining packets to vPath.
Cisco Virtual Security Gateway
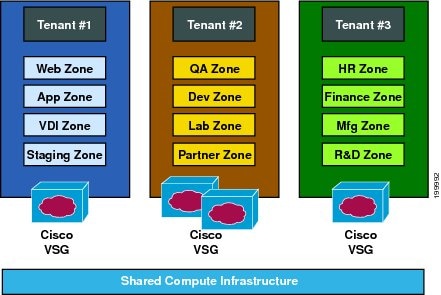
The Cisco Virtual Security Gateway (VSG) is a virtual firewall appliance that provides trusted access to virtual data center and cloud environments. The Cisco VSG enables a broad set of multitenant workloads that have varied security profiles to share a common compute infrastructure in a virtual data center private cloud or in a public cloud. By associating one or more virtual machines (VMs) into distinct trust zones, the Cisco VSG ensures that access to trust zones is controlled and monitored through established security policies.
Integrated with the Cisco Nexus 1000V Series switch and running on the Cisco NX-OS operating system, the Cisco VSG provides the following benefits :
- Trusted Multitenant Access—Granular, zone-based control and monitoring with context-aware security policies applied in a multitenant (scale-out) environment to strengthen regulatory compliance and simplify audits. Security policies are organized into security profile templates to simplify their management and deployment across many Cisco VSGs.
- Dynamic operation—On-demand provisioning of security templates and trust zones during VM instantiation and mobility-transparent enforcement and monitoring as live migration of VMs occur across different physical servers.
- Nondisruptive administration—Administrative segregation across security and server teams while enhancing collaboration, eliminating administrative errors, and simplifying audits.
The Cisco VSG provides the following advantages:
- Enhances compliance with industry regulations
- Simplifies audit processes in virtualized environments
- Reduces cost by securely deploying a broad set of virtualized workloads across multiple tenants on a shared compute infrastructure, whether in virtual data centers or private/public cloud computing environments
Cisco Adaptive Security Virtual Appliance
The Adaptive Security Virtual Appliance is a virtualized network security solution based on the market-leading Cisco ASA 5500-X Series firewalls. It supports both traditional and next-generation software-defined network (SDN) and Cisco Application Centric Infrastructure (ACI) environments to provide policy enforcement and threat inspection across heterogeneous multi-site environments.
Features and capabilities
1. Purpose Built for Data Center Security
The Adaptive Security Virtual Appliance brings full ASA firewall and VPN capabilities to virtualized environments to help safeguard traffic and multitenant architectures. Optimized for data center deployments, it’s designed to work in multiple hypervisor environments, reduce administrative overhead, and increase operational efficiency.
Virtual-switch independent, it may be deployed in Cisco, hybrid, and non-Cisco based data centers. VMware, KVM, Hyper-V, Amazon Web Services, and other cloud platforms offer flexibility and choice.
Predetermined configurations accelerate and simplify security service provisioning to match the speed of application deployment. These configurations provide the appliance with critical security functions that dynamically scale to protect assets as business demands change.
2. Fully Integrated ACI Security
The appliance has been fully and transparently integrated into the fabric of the next-generation Application Centric Infrastructure data center architecture. For those deployments, the Cisco Application Policy Infrastructure Controller provides a single point of control for both network and security management. It can provision the appliance’s security as a service, manage policy, and monitor the entire network and security environment for a unified view. This approach removes the limitations of traditional network-oriented security solutions, allowing for significantly streamlined provisioning.
In the ACI topology-independent environment, ASAv services are managed as a pool of security resources. These resources can be selected and attached to specific applications or transactions to provide dynamic, scalable, policy-based security.
3. Management Options
The virtual appliance, along with the physical ASA 5500-X Next Generation Firewalls can be managed by security administrators as a pool of resources that scale on demand. It provides programmable automation for deployment and management and uses a common policy-based operational model across physical and virtual environments, reducing cost and complexity.
Management options include the following.
Representational State Transfer (REST) application programming interface (API): This API simplifies device management; integrating the virtual appliance with custom policy orchestration systems used in SDN environments.
Cisco Security Manager: You can use this solution for comprehensive multi-device deployment and management of both the virtual appliance and the physical ASA 5500-X appliances. You gain a consolidated view of the entire firewall and VPN policy across the network.
Cisco Adaptive Security Device Manager: This no-cost GUI-based single-device management option can be used for configuring, monitoring, and troubleshooting the virtual and physical appliances.
Command-line interface: A flexible command-based management interface uses scripting for quick provisioning and automation of the appliances.
Cisco Cloud Service Router 1000v
The Cisco CSR 1000v Cloud Services Router provides a cloud-based virtual router deployed on a virtual machine (VM) instance on x86 server hardware. It supports a subset of Cisco IOS XE software features and technologies, providing Cisco IOS XE security and switching features on a virtualization platform.
When the Cisco CSR 1000v is deployed on a VM, the Cisco IOS XE software functions just as if it were deployed on a traditional Cisco hardware platform.
Features
The Cisco CSR 1000v includes a virtual Route Processor and a virtual Forwarding Processor (FP) as part of its architecture. It supports a subset of Cisco IOS XE software features and technologies.
The Cisco CSR 1000v can provide secure connectivity from an enterprise location, such as a branch office or data center, to the public or private cloud.
The Cisco CSR 1000v is deployed as a virtual machine on a hypervisor. Optionally, you can use a virtual switch (vSwitch), depending on your deployment. You can use selected Cisco equipment for some components. The supported components will depend on your software release.
Benefits of Virtualization Using the Cisco CSR 1000v Series Cloud Services Router
The Cisco CSR 1000v Series uses the benefits of virtualization in the cloud to provide the following:
- Hardware independenceBecause the Cisco CSR 1000v runs on a virtual machine, it can be supported on any x86 hardware that the virtualization platform supports.
- Sharing of resourcesThe resources used by the Cisco CSR 1000v are managed by the hypervisor, and resources can be shared among VMs. The amount of hardware resources that the VM server allocates to a specific VM can be reallocated to another VM on the server.
- Flexibility in deploymentYou can easily move a VM from one server to another. Thus, you can move the Cisco CSR 1000v from a server in one physical location to a server in another physical location without moving any hardware resources.
Citrix NetScaler 1000V
It is an application delivery controller solution, and part of the Cisco Cloud Network Services architecture. It gives applications critical performance enhancements, including offloading application servers, helping guarantee quality of service (QoS), and improving end-user experiences.
Features and capabilities
deploy the Citrix NetScaler 1000V on demand, anywhere in the data center, using the Cisco Nexus 1100 Series Cloud Services Platform (CSP) with Hardware SSL offload or running as a virtual appliance on ESXi or KVM. When running on KVM, you can integrate it with OpenStack using the Cisco Prime Network Services Controller.
The simplicity and flexibility of the NetScaler 1000V make it cost-effective to fully optimize every web application and more effectively integrate networking services with application delivery.
Integrating the Citrix Netscaler 1000V with Cisco ACI
Cisco Application Centric Infrastructure (ACI) supplies the critical link between business-based requirements for applications and the infrastructure that supports them. The Citrix NetScaler 1000V connects infrastructure and applications. It makes their configuration available to the Cisco Application Policy Infrastructure Controller (APIC) through integration.
Citrix NetScaler 1000V and Cisco ACI help data center and cloud administrators to holistically control Layer 2 to Layer 7 network services in a unified manner. You do this through seamless insertion and automation of best-in-class NetScaler 1000V services into next-generation data centers built on Cisco's ACI architectures.
NetScaler 1000V uses the APIC to programmatically automate network provisioning and control on the basis of application requirements and policies for both data center and enterprise environments. Cisco ACI defines a policy-based service insertion mechanism for both physical and virtual NetScaler 1000V appliances.
Cisco Virtual Wide Area Application Services
Cisco Virtual WAAS (vWAAS) is the first cloud-ready WAN optimization solution that accelerates applications delivered from private and virtual private cloud infrastructure, using policy-based on-demand orchestration.
Cisco vWAAS can be:
- Virtualized on the industry-leading VMware ESX and ESXi hypervisor
- Deployed on Cisco Unified Computing System x86 servers in an on-demand, elastic, and multitenant manner
- Integrated with Cisco Nexus 1000V, which optimizes application delivery in a virtual machine environment through Cisco vPath architecture services.
Cisco vWAAS Benefits
Cisco vWAAS is designed for both enterprises and service providers to offer private and virtual private cloud-based application delivery service over the WAN. vWAAS provides:
- On-demand orchestration of WAN optimization
- Fault tolerance with virtual machine (VM) mobility awareness
- Lower operating expenses for customers who are migrating their applications to the cloud
Cisco vWAAS Advantages
Cisco vWAAS is a WAN optimization service that gets deployed in an application-specific, virtualization-aware, and on-demand manner. This solution:
- Uses policy-based configuration in the Cisco Nexus 1000V to associate with server VMs as they are instantiated or moved
- Helps enable cloud providers to offer rapid creation of WAN optimization services in cloud-based environments
- Supports transparent deployment at the network edge using WCCP providing deployment flexibility and feature consistency
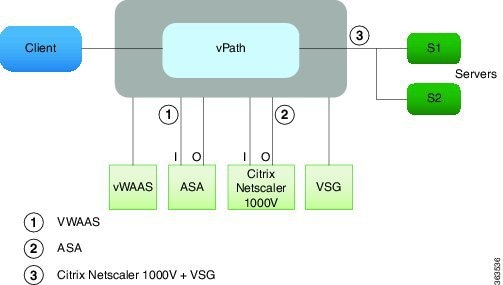
vPath Service Chains
Service chaining allows multiple service nodes to be included in a service path so that the packets that belong to a particular flow can travel through all the virtual service nodes in the sevice chain. Each service node in a chain uses the security profile specified in the vservice command for that VSN.
A service path consists of an ordered list of services to be applied to a packet flow and it is used to define the service chain. When a packet reaches a virtual machine with vPath service chaining enabled, vPath intercepts the packet and redirects the packet to multiple VSNs in a specified order.
vPath thus acts as an orchestrator of the chain to deliver multiple services and VNMC enables the provisioning of service chains.
Cisco VACS Containers
- A Cisco Cloud Services Router (CSR) 1000V virtual router with multiple networks on which workloads are placed and a single uplink with a Layer 3 connection to the datacenter network.
- A Cisco Virtual Services Gateway (VSG) zone-based firewall to control and monitor segmentation policies within the networks.
A Cisco prime Network Services Controller (PNSC) that defines and monitors the zone policies. A PNSC can span across multiple containers and the security policy configuration is done by PNSC.
Each container is provided switching by one Cisco Nexus 1000V switch. The Cisco Nexus 1000Vswitch instantiates the networks as port profiles. A single Cisco Nexus 1000V switch can provide switching for multiple containers.
Types of Cisco VACS Container Templates
The Cisco Virtual Application Services (Cisco VACS) three tier internal container template offers a preset collection of virtual resources that you can deploy in your datacenter. The internal template defines and enforces the overall policy in the web, application, and database tiers on a shared VLAN or VXLAN and achieves minimum required segregation and enables you to choose a private or public address on the gateway. This template enables you to have external connectivity only to the web tier and restricts the application and database tiers from exposing their services or from consuming the services exposed by other applications inside a firewall.
The three tier internal container template uses Enhanced Interior Gateway Routing Protocol (EIGRP) as the default routing protocol if you choose the Public Router IP type. However, you have an option to choose either the EIGRP protocol or set up Static Routing Protocol, and set up other static routes to forward upstream traffic to the container's internal network.
2. Three Tier External Container template
The Cisco VACS 3 Tier external container template retains all features of a 3 tier Internal template and also allows external access to application and database tiers in addition to the web tier .This template type allows you to expose the services of the container to external applications and consume the services exposed by other applications behind the firewall. As with the internal template type, the specific security profile requirements for the tiers are enabled by the zone ans security policies.
3. Custom Container template
The Cisco Virtual Application Container Services (Cisco VACS) Custom Container (or Advanced Container) template enables you to design a container that meets your specific requirements without any restrictions on the number of tiers, zones, network, and application types. The custom container type allows you to build a template that allows an n-tier application with each tier on a shared or dedicated VLAN or VXLAN segments.
The Cisco Virtual Application Container Services Cisco VACS guidelines and limitations are as follows:
- Cisco VACS supports only a new installation of the Cisco Nexus 1000V and Cisco PNSC.
Cisco VACS supports Cisco UCS Director, Release 5.1 and the following versions of the related components: - You can add or edit a container template, and then instantiate containers from the template.
- Cisco VACS supports VMware ESX 5.0, 5.1, and 5.5 and VMware vCenter 5.1 and later versions. We recommend that you use vCenter version 5.5 because it is compatible with all versions of VMware ESXi.
- The number of virtual machines that you can add to a container template is limited only by the hardware of your setup.
The Cisco Virtual Application Container (Cisco VACS) template has the following prerequisites:
- Set up a VMware vCenter account on Cisco UCS Director.
- Define the Network Policy. A network policy includes the VLAN pool policy, the VXLAN pool policy, Statis IP pool policy, and the IP Subnet pool policy.
- Define the Computing Policy. Computing policies determine the computing resources used during provisioning that satisfy group or workload requirements.
- Define the Storage Policy. A storage policy defines resources, such as the datastore scope, type of storage to use, minimum conditions for capacity, and latency. The storage policy also provides options to configure additional disk policies for multiple disks and to provide datastore choices for use during a service request creation.
- Define the Systems Policy. A system policy defines the system-specific information, such as the template to use, time zone, and operating system-specific information.
No comments:
Post a Comment