Describe Infrastructure Virtualization
Difference between vSwitch and VDS
The VDS extends the features and capabilities of virtual networks while simplifying provisioning and the ongoing configuration, monitoring and management process.
vSphere network switches can be divided into two logical sections: the data plane and the management plane. The data plane implements the packet switching, filtering, tagging and so on. The management plane is the control structure used by the operator to configure data plane functionality. Each vSphere Standard Switch (VSS) contains both data and management planes, and the administrator configures and maintains each switch individually.
The VDS eases this management burden by treating the network as an aggregated resource. Individual host-level virtual switches are abstracted into one large VDS spanning multiple hosts at the data center-level. In this design, the data plane remains local to each VDS but the management plane is centralized.
Each VMware vCenter Server instance can support up to 128 VDSs; each VDS can manage up to 500 hosts.
Additional Details:
- Distributed Virtual Port Groups (DV Port Groups) — Port groups that specify port configuration options for each member port
- Distributed Virtual Uplinks (dvUplinks) — dvUplinks provide a level of abstraction for the physical NICs (vmnics) on each host
- Private VLANs (PVLANs) — PVLAN support enables broader compatibility with existing networking environments using the technology
- Network vMotion — Simplifies monitoring and troubleshooting by tracking the networking state (such as counters and port statistics) of each virtual machine as it moves from host to host on a VDS
- Bi-directional Traffic Shaping — Applies traffic shaping policies on DV port group definitions, defined by average bandwidth, peak bandwidth and burst size
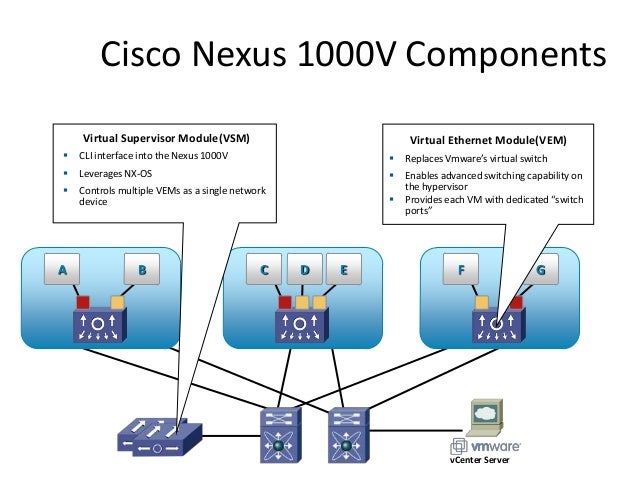
Cisco Nexus 1000V components
Cisco Nexus 1000V Series Switches are virtual machine access switches that are an intelligent software switch implementation based on IEEE 802.1Q standard for VMware vSphere environments running the Cisco NX-OS Software operating system. Operating inside the VMware ESX hypervisor, the Cisco Nexus 1000V Series supports Cisco VN-Link server virtualization technology to provide:
- Policy-based virtual machine connectivity
- Mobile virtual machine security and network policy
- Non-disruptive operational model for server virtualization and networking teams
- VXLAN based overlays for physical topology independent L2 segments
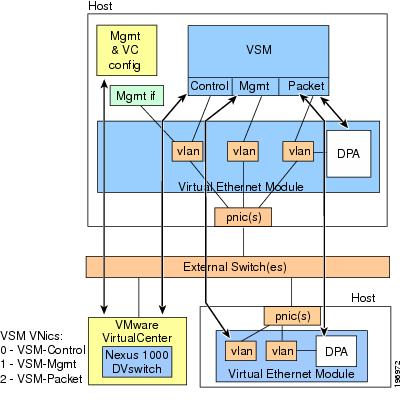
Virtual Ethernet Module (VEM)
The Cisco Nexus 1000V Series VEM runs as part of the VMware ESX or ESXi kernel and replaces the VMware virtual switch (vSwitch). This level of integration helps ensure that the Cisco Nexus 1000V Series is fully aware of all server virtualization events, such as VMware vMotion and Distributed Resource Scheduler (DRS). The VEM takes configuration information from the VSM and provides advanced networking functions: quality of service (QoS), security features, and monitoring features.
Virtual Supervisor Module (VSM)
The Cisco Nexus 1000V Series VSM controls multiple VEMs as one logical modular switch. Configuration is performed through the VSM and is automatically propagated to the VEMs. Instead of configuring soft switches inside the hypervisor on a host-by-host basis administrators can define configurations for immediate use on all VEMs being managed by the VSM from a single interface.
VSM appliance
The Cisco Nexus 1010 and Cisco Nexus1010-X VSAs are appliances that can provide improved management and scalability in Cisco Nexus 1000V Series Switches and VMware vSphere deployments. TheCisco Nexus 1000V Series can be deployed exclusively as software running in a VMware ESX or ESXi cluster; however, the Cisco Nexus 1010 and 1010-X VSAs provide customers with an additional deployment option with several benefits. The VSAs are used to manage and host the Cisco Nexus 1000V Series Virtual Supervisor Modules (VSMs) that control the Cisco Nexus 1000V Series Virtual Ethernet Modules (VEMs), which reside in the hypervisor of the host server. Also, the Cisco Nexus 1010 and 1010-X can host a variety of virtual network services, including the Cisco Prime Network Analysis Module (NAM) for Nexus 1010, Cisco Virtual Security Gateway (VSG) for Nexus 1000V Series Switch, and Cisco Data Center Network Manager (DCNM).
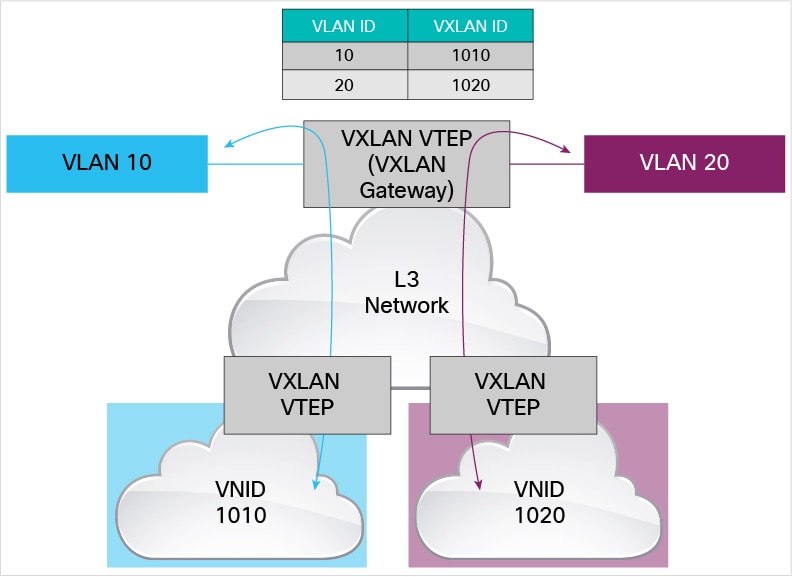
Difference between VLAN and VXLAN
As its name indicates, VXLAN is designed to provide the same Ethernet Layer 2 network services as VLAN does today, but with greater extensibility and flexibility. Compared to VLAN, VXLAN offers the following benefits:
Flexible placement of multitenant segments throughout the data center: It provides a solution to extend Layer 2 segments over the underlying shared network infrastructure so that tenant workload can be placed across physical pods in the data center.
Higher scalability to address more Layer 2 segments: VLANs use a 12-bit VLAN ID to address Layer 2 segments, which results in limiting scalability of only 4094 VLANs. VXLAN uses a 24-bit segment ID known as the VXLAN network identifier (VNID), which enables up to 16 million VXLAN segments to coexist in the same administrative domain.
Better utilization of available network paths in the underlying infrastructure: VLAN uses the Spanning Tree Protocol for loop prevention, which ends up not using half of the network links in a network by blocking redundant paths. In contrast, VXLAN packets are transferred through the underlying network based on its Layer 3 header and can take complete advantage of Layer 3 routing, equal-cost multipath (ECMP) routing, and link aggregation protocols to use all available paths.
Higher scalability to address more Layer 2 segments: VLANs use a 12-bit VLAN ID to address Layer 2 segments, which results in limiting scalability of only 4094 VLANs. VXLAN uses a 24-bit segment ID known as the VXLAN network identifier (VNID), which enables up to 16 million VXLAN segments to coexist in the same administrative domain.
Better utilization of available network paths in the underlying infrastructure: VLAN uses the Spanning Tree Protocol for loop prevention, which ends up not using half of the network links in a network by blocking redundant paths. In contrast, VXLAN packets are transferred through the underlying network based on its Layer 3 header and can take complete advantage of Layer 3 routing, equal-cost multipath (ECMP) routing, and link aggregation protocols to use all available paths.
Virtual networking services
Advantages of virtualized networks:
- Elasticity (Scale Up and Out)
- Pay as you grow model
- Orchestration (Ease of Automation)
- Minimal Cross-Tenant Dependencies
Cisco Cloud Networking Services:
- Cisco Virtual Application Container Services
- Citrix NetScaler 1000V
- Cisco Virtual Wide Area Application Services (vWAAS)Cisco Prime Virtual Network Analysis Module (vNAM)
- Cisco ASA 1000V Cloud Firewall
- Cisco Virtual Security Gateway for Nexus 1000V Switch
- Cisco Cloud Services Router 1000V Series
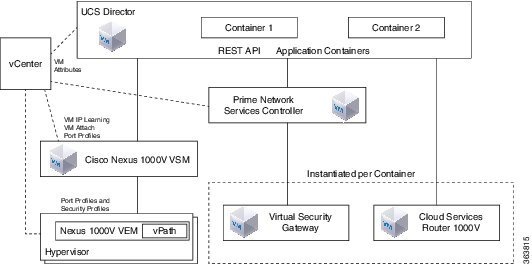
Cisco Prime Network Services Controller – a major element of many Cisco enterprise networking solutions. Through a single pane, you can automate virtual network management to execute configuration changes quickly and consistently. This gives your staff more time to optimize the network environment.
Define Virtual Application Containers
Cisco Virtual Application Container Services (Cisco VACS) is a software solution that automates the coordinated licensing, installation, and deployment of multiple virtual services in your datacenter to enable you to easily and efficiently set up virtualized applications.
- Cisco Nexus 1000V
- Cisco Prime Network Services Controller (PNSC)
- Cisco Cloud Services Router (CSR)1000V
- Cisco Virtual Security Gateway (VSG)
Cisco VACS provides ready-to-use application container templates that define the rules for a collection of virtual machines (VMs) within an internal network and a firewall. An application container is a set of virtual services, such as routers, firewalls, and other network devices configured in a consistent manner, to deploy different workloads. When you create and instantiate an application container, Cisco VACS deploys the VMs, and configures the networks, the firewall, the virtual switches, and enables quick provisioning of network and security at the virtual layer.
Cisco UCS Director will act as the management interface to deploy, provision, and monitor the Cisco VACS solution.
Three-tier application container
The Cisco Virtual Application Services (Cisco VACS) three tier internal container template offers a preset collection of virtual resources that you can deploy in your datacenter. The internal template defines and enforces the overall policy in the web, application, and database tiers on a shared VLAN or VXLAN and achieves minimum required segregation and enables you to choose a private or public address on the gateway. This template enables you to have external connectivity only to the web tier and restricts the application and database tiers from exposing their services or from consuming the services exposed by other applications inside a firewall.
The three tier internal container template uses Enhanced Interior Gateway Routing Protocol (EIGRP) as the default routing protocol if you choose the Public Router IP type. However, you have an option to choose either the EIGRP protocol or set up Static Routing Protocol, and set up other static routes to forward upstream traffic to the container’s internal network
Custom container
A set of virtual network devices that work in conjunction to provide connectivity to a single tenant network.
No comments:
Post a Comment